uSecure Logs Storage and Management System
Log gathering ‧ Central storage ‧ Retrieval and search
Providing logging and log storage mechanisms for compliance to satisfy the needs of organizations and enterprises for information security governance and auditing.
Timely Insights into Emerging Information Security Threats in Big Data
Event source records and data in the corporate environment are gathered to allow for timely search and compilation of information security-related records through big data, facilitating the management of digital footprints.
- Obtain comprehensive log intelligence for at-a-glance information on device use
- Ensure logging integrity to help enterprises store information security event trajectories
- Provide decentralized management and simplified searching to meet auditing and compliance needs
- Featuring an intuitive visual dashboard to enhance management convenience
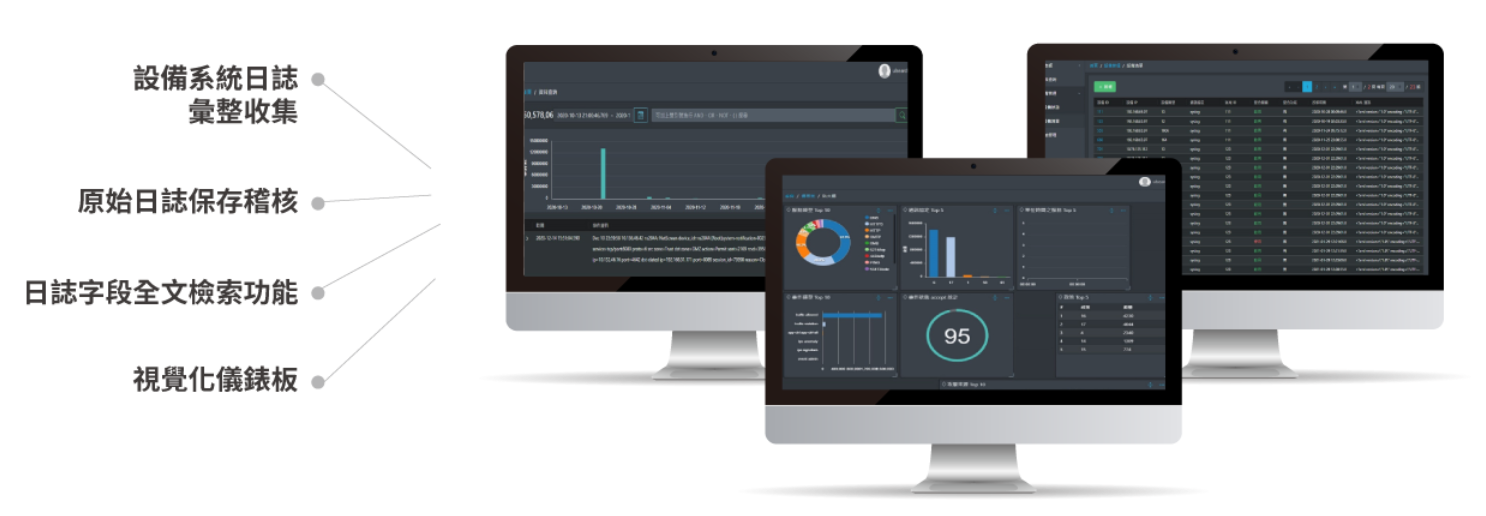
Logging・Complete Log Storage
Integration with various logging channels
Various gathering capabilities are provided to effectively integrate different log output methods for application systems and information security devices, achieving central logging.
Storage mechanism ensuring the integrity of raw logs
- Regularly encapsulate, encrypt, and store raw logs
- Create fingerprinting records for raw log files using the SHA256 algorithm
- Verify the integrity of archived raw log files through specific mechanisms
- Make sure that file contents are not altered
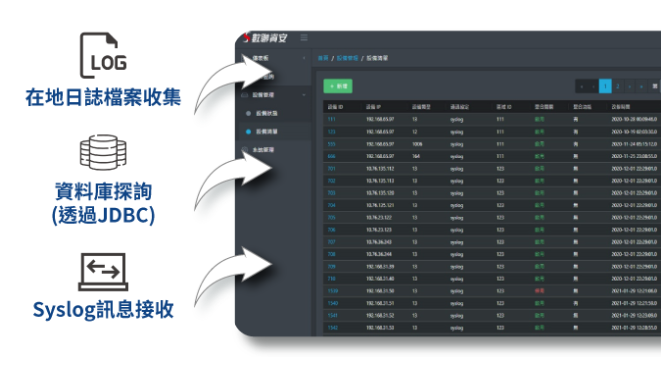
Decentralized Management・Simplified Searching
Providing log field and full text search functions
- Search certain events on systems or devices using keywords.
- Specify a visualized time period in which to search to help investigate and analyze the occurrence and frequency of events
- Provide a search command bar that supports complex computing and provides multi-layer filters to narrow down the search scope and get more accurate search results
Built-in role-based authorization functions
- Configure the functions available to roles
- Restrict the retrieval of certain equipment items by roles
- Grant appropriate authority for log searching to departments according to their needs on a need-to-know basis
