Security Operations Center (SOC)
Data-driven monitoring can control network status in real time, identify risks in a timely manner, ensure safe system operation.
Ensure that your data and network activities are optimally protected.
ISSDU received the highest A-Plus SOC Service Provider rating!
The first in the industry to pass three ISO certifications
Taiwan’s only SOC service provider with leading big data technology that integrates intelligence platforms to strengthen intelligence collection for stronger warning and response capabilities.
billion +
billion +
Attacks blocked per monthly
+
Number of customers served

Full Integration and Automation
Pre-Incident Prevention
Prevention
Digital Intelligence Consulting Service
Digital asset inventory
Collection of darknet and attack information
Integration and verification of threat intelligence
During-Incident Monitoring and Reinforcement
Monitoring and Reinforcement
NG-SOC and MDR Monitoring Services
Network monitoring and endpoint event trajectory analysis
Enhanced capabilities for event sourcing, association analysis of heterogeneous data, and intelligence integration and interpretation for faster response
Post-Incident Response and Investigation
Response and Investigation
Information security incident response (IR) service
Provision of evidence of information security incidents
Threat hunting and eradication

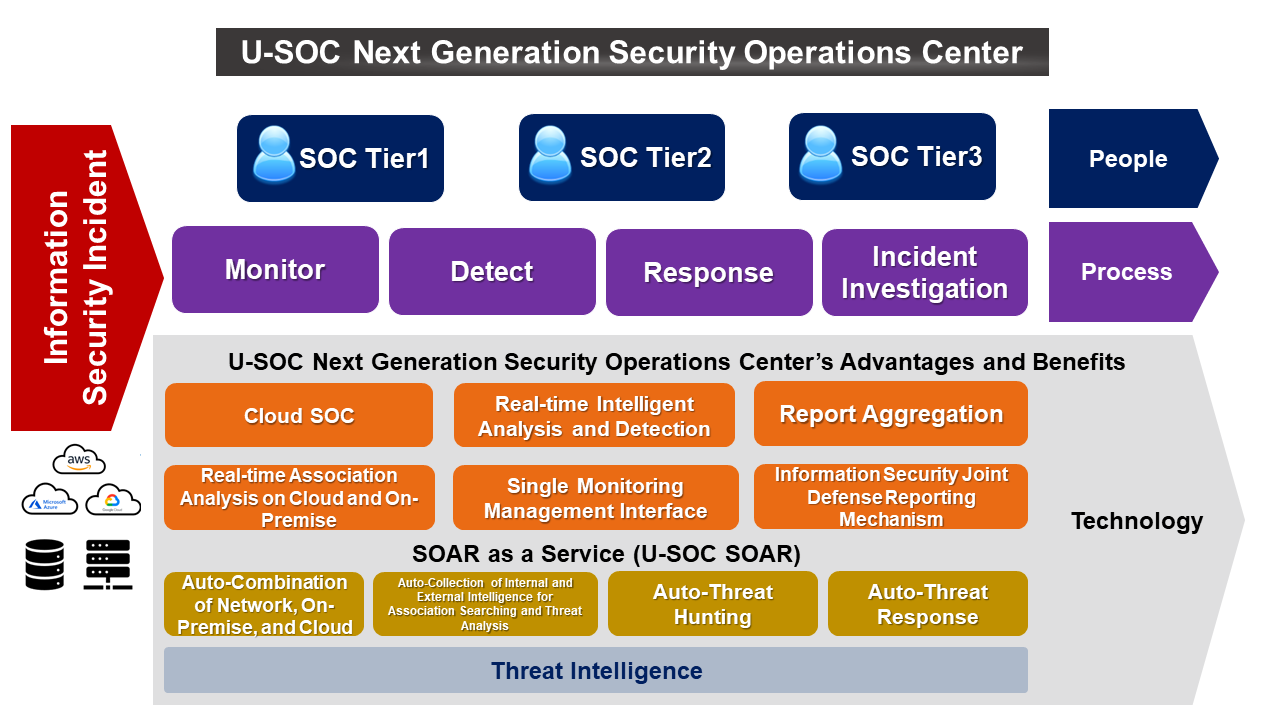
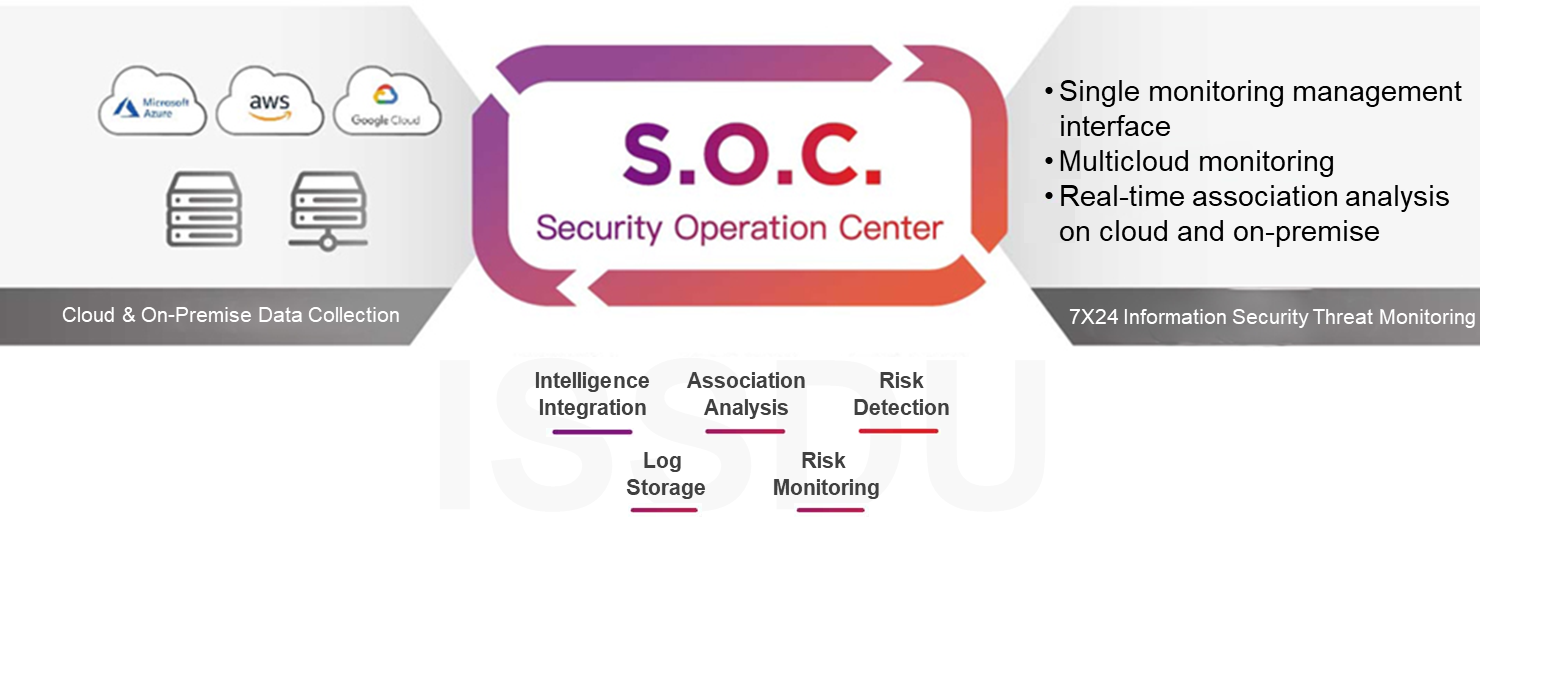
Cloud SOC
01
Intelligence-Driven
Use big data platforms as the core to gather various types of information, accelerating association detection, analysis, and identification
02
Real-time Intelligent Analysis and Detection
Utilize machine learning to improve the completeness and accuracy of detection and interpretation based on association rules
03
Auto-Reporting and Threat Response
Control the process from event reporting to closure through auto-response scripts, effectively reducing response time
04
Comprehensive Cloud SOC
Integrate hybrid multicloud log collection and storage to increase threat visibility
05
Real-time Association Analysis on Cloud and On-Premise
Perform timely collaborative association analysis and joint defense measures for information security anomalies or threats on the cloud and on-premise
06
Single Monitoring Management Interface
Monitor multicloud and on-premise environments with a single interface to reduce management costs.
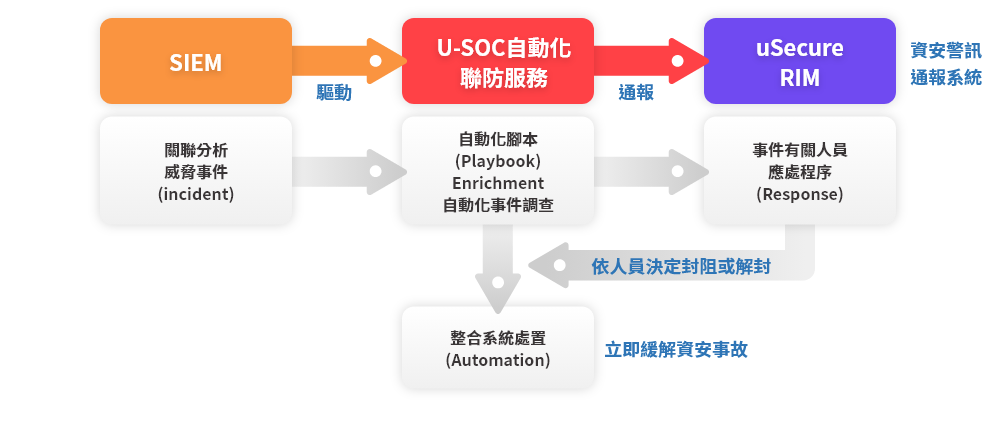
U-SOC SOAR
Improving efficiency with SOAR for more powerful defense
U-SOC SOAR can create integrated templates for defense in depth (DiD) based on different required scenarios and customer needs to effectively achieve automation, detection, investigation, and timely joint defense, thereby reducing information security risks and improving operation efficiency.
Orchestration
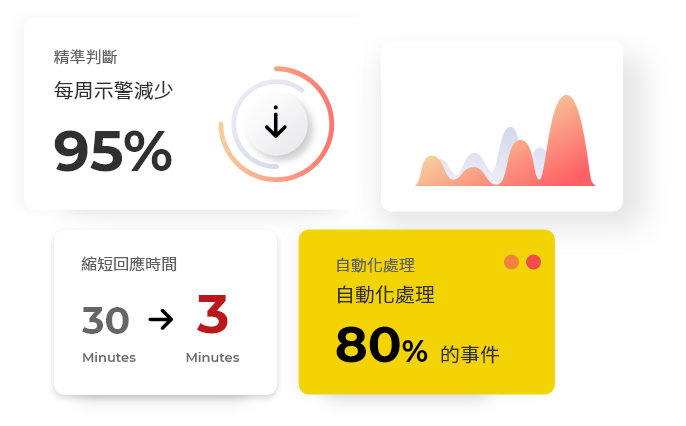
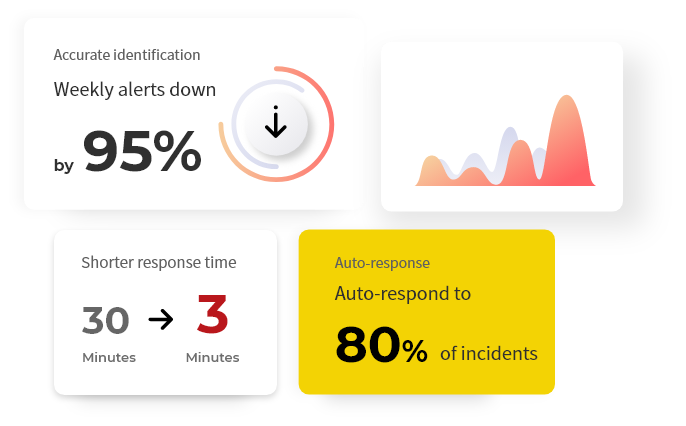
Weekly alerts down by 95% with accurate identification
Integrate network, on-premise, and cloud, combine different scenarios or information security devices and systems, and carry out auto-investigation of incidents to integrate personnel, procedures, and technology.
Automation
Shorter response time
Automate the analysis of threat events, achieve secondary auto-association investigation and timely joint defense, and ensure quick incident response, reducing response time from 30 minutes to 3 minutes.
Response
Auto-respond to 30% of incidents
Carry out auto-investigation of incidents to integrate personnel, procedures, and technology, reducing the consumption of human resources for incident investigation and analysis and increasing incident response speed and accuracy.
Managed Detection and Response (MDR) Assisting Enterprises in Information Security Incident Response
- Strengthened endpoint protection for the effective blocking of threats and attacks
- Comprehensive event analysis and assessment advice to increase enterprises’ information security resilience
-
Integration of SOC with the MDR service to enhance threat visibility

More Value-added Services
Digital Intelligence Consulting Service
ISSDU integrates with external platforms and conducts research to develop strong intelligence collection capabilities and provide information on potential fraudulent websites as well as other intelligence related to your organization. After systems or platforms generate relevant warnings, the ISSDU consulting team will verify them and provide relevant monthly reports.
Collection and Analysis of Darknet Intelligence
This service collects a large amount of raw intelligence through various channels and methods. After analysis and verification by our consulting service team, we extract intelligence on threats against your organization.
Detection of Fraudulent Websites
This service assists enterprises in detecting fraudulent websites. By checking the URL similarity of websites and analyzing website content, it generates a list of suspicious websites, provides analysis results, IOC, and response advice, and immediately notifies relevant personnel for handling.