uSecure SIP Security Intelligence Platform
Turning complexity into simplicity to grasp information security threats
With security information and event management at its core, this SIEM platform
combines log management and analysis
Huge volumes of events are turned into easy-to-grasp visual information security intelligence through intelligent and efficient analysis.

Timely Insights into Emerging Information Security Threats in Big Data
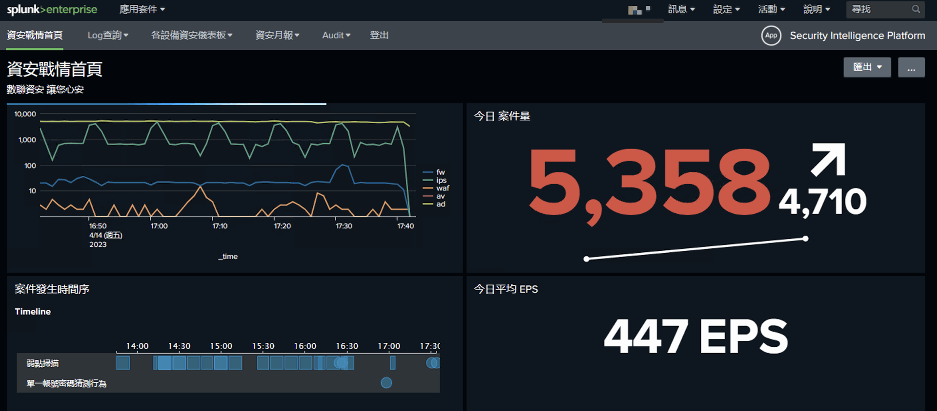
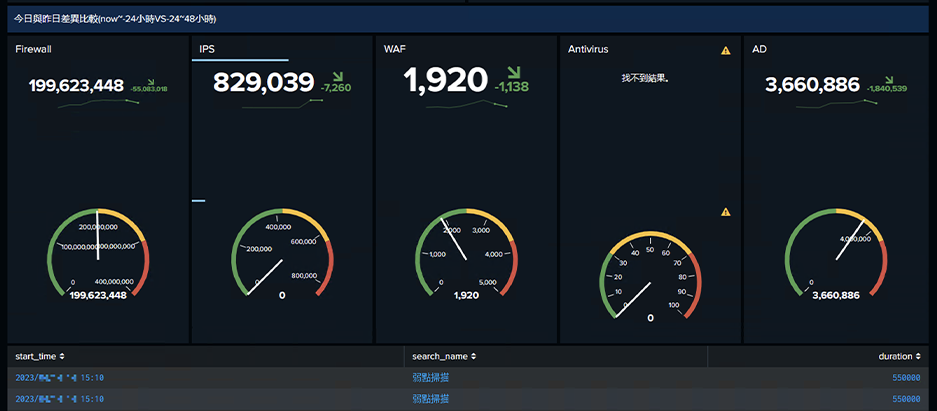
Splunk, a SIEM solution, is used to gather event source records and data in the corporate environment for timely search, compilation, monitoring, and analysis of information security-related records through big data, quickly identifying threats.
Five Upgraded Information Security Capabilities to Accurately Spot Information Security Threats
Big data analysis and AI technology are used to extract helpful information security intelligence visualized in graphs, better helping information security managers effectively obtain accurate information security intelligence from huge volumes of complex data as well as respond to and deal with information security threat events in a timely manner, as compared to traditional SIEM.
01
Collaboration
Information security personnel can maintain information security on SIEM, forming a complete security operations center (SOC).
02
Visibility
Relational visualization approaches are provided for quick event searching and intelligence collection.
03
Management
Complete information security event reporting and assignment mechanisms are in place to avoid interrupting the handling of information security events.
04
Accuracy
SIEM technology is integrated with big data to extract critical information security threat intelligence, pinpointing potential threats.
05
Alertness
Unusual behavior and threats are detected beforehand through associational analysis to allow for early preventive decision-making.
With Splunk's Big Data Platform as the Core
- Splunk has been recognized by Gartner as a leading brand in SIEM for 9 consecutive years (2014-2022).
- Use an AI event association engine together with big data algorithms to analyze a large amount of information in order to identify unknown possible threats, helping enterprises make early predications and take preventive action.
- Understand when hackers intruded through historical data lookback and trajectory data analysis by linking the latest information security intelligence, in order to detect anomalous changes early.

Efficient Security Event Management by Collecting and Compiling Information Security Intelligence
- Support multiple security devices, operating systems, and applications systems, allow for fast collection of various logs without subprograms or languages, and provide trouble-free integration of information security devices into uSecure SIP.
- Use an AI event association engine together with big data algorithms to analyze a large amount of information in order to identify unknown possible threats, helping enterprises make early predications and take preventive action.
- Understand when hackers intruded through historical data lookback and trajectory data analysis by linking the latest information security intelligence, in order to detect anomalous changes early.